
We have read the news stories: an attacker gains access to a networked system at some company or hospital or government agency. The system owner has lost control. That system now serves the attackers. Will the attacker steal information? Destroy data? Hold the system for ransom? Damage property? The attacker gets to choose.
The experts have been telling us about the problem for years. In our connected world, everybody's connected to the Internet, directly or indirectly. That means we are potentially connected to every hacker, criminal, and spy on earth. CIA Director George Tenet put it this way:
"Think about it for a moment – we share the same network with our adversaries." [1]
Director Tenet spoke of "our adversaries" — and the word fits. The people who take over your systems for their own purposes are definitely not your friends.
The process begins with a system compromise, where an unauthorized person gains access. This eventually leads to cyber exploits, where intruders steal data; and cyber attacks, which destroy or disrupt the target systems.
Very often, a single system is compromised, after which the attackers quietly reach out to access more and more resources on your network. During this exploration your systems continue doing their usual work, even while the attackers have the option to act at any time they choose.
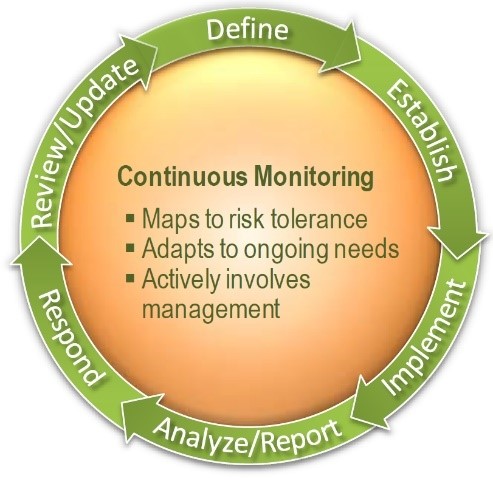
Image Credit: NIST
Modern information security works to protect systems and networks, preventing and reducing harm with three general practices:
- Establishing secure configurations, to block the most common and well-known methods of compromise.
- Subscribing to and monitoring vulnerability notices from government and industry, so that the system operators can update software and system configurations promptly, to correct newly-discovered vulnerabilities before an intruder takes advantage of them.
- Performing continuous monitoring of your systems and networks, allowing your operators to detect and identify attacks and vulnerabilities. With rapid detection, the operators may be able to act before an intruder actually completes a compromise, exploit, or attack. Without it, the problem is detected too late.
Industry and government have embedded these practices in structured 'frameworks' that give a full spectrum of cybersecurity activities, establishing and maintaining effective information security for a system and its connected networks. Some well-known frameworks are:
- For Federal Government agencies: the Risk Management Framework (RMF), part of the FISMA Implementation Project at the National Institute of Standards and Technology (NIST).
- For the payments industry: the Payment Card Industry Data Security Standard (PCI).
- For the healthcare industry: the HIPAA Security Rule, which covers electronic protected health information
Each framework provides detailed guidance on the implementation of all the recommended practices. For example, NIST Special Publication 800-137 describes recommended practices for continuous monitoring.
As you can see, information security is part of a large picture with many moving parts. Contact Vision for more information about Information Security and how we can help you protect your systems while complying with government regulations and industry standards.
[1] ''Information Security Risks, Opportunities, and the Bottom Line'' — Remarks of the Director of Central Intelligence George J. Tenet at the Sam Nunn Nations Bank Policy Forum, Georgia Institute of Technology, Atlanta, April 6, 1998.
[2] NIST Special Publication 800-137, Information Security Continuous Monitoring (ISCM) for Federal Information Systems and Organizations, September, 2011. https://csrc.nist.gov/publications/detail/sp/800-137/final